As hotels adopt more digital tools like online check-ins and smart room controls, their exposure to cyber threats is growing. This article explores the latest trends, statistics and strategies shaping hospitality cybersecurity in 2025.
Hospitality Cybersecurity Risks in 2026
Digital transformation has empowered hospitality — from hotels and resorts to restaurants and cruise ships — but it has also widened the attack surface.
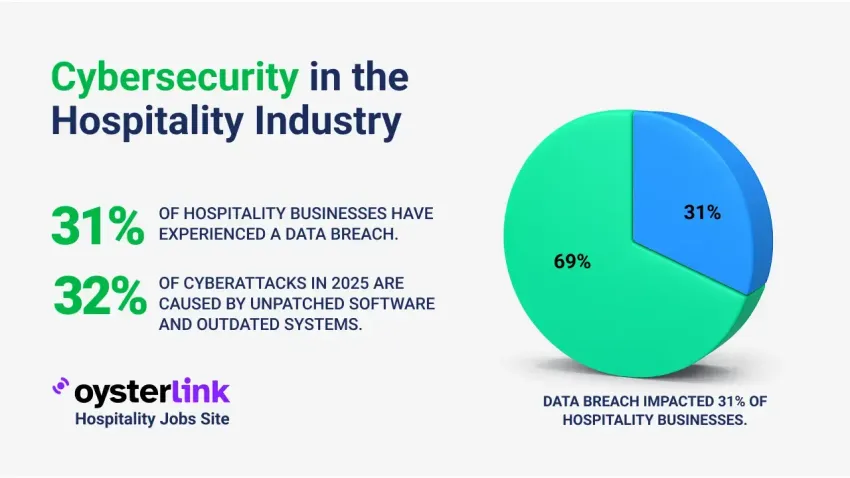
According to a report, 31% of hospitality organizations globally have experienced a data breach, with 89% of those suffering repeat breaches within a single year.
The average cost per breach surged to $3.36 million in 2023, up from $2.94 million in 2022.
Additionally, Trustwave flags over 14,000 publicly exposed vulnerabilities in hospitality systems, with 61.5% of breaches traced to these openings.
These statistics underscore that cybersecurity in hospitality industry operations isn’t optional — it’s mission-critical and financial and reputational risks are growing.
Trends in Hospitality Cybersecurity
Cyber threats in hospitality are shifting fast. Here’s what’s shaping hotel cybersecurity in 2025.
AI-Powered Attacks
One of the most pressing cybersecurity trends in hospitality for 2025 is the rise of AI-powered attacks.
Generative AI is being used to automate phishing schemes, voice scams and malware creation with alarming precision.
In fact, 50% of cybersecurity executives believe AI will significantly escalate adversary capabilities this year.

A notable example is the MGM Resorts breach in September 2023, which reportedly caused over $100 million in damages and was driven by AI-enhanced social engineering and phishing tactics.
As these threats grow more sophisticated, hospitality businesses must implement real-time defenses — including voice authentication filters and deepfake detection — while also ensuring staff receive consistent training to counter social engineering.
Human & Machine Blurring
With employee churn and interconnected systems, the risk of credential misuse continues to rise.
By 2025, an estimated 70% of hotel staff will have access to sensitive systems without receiving consistent cybersecurity training.

Meanwhile, the expanding "identity surface" — including IoT devices, PMS integration and machine accounts — requires hotels to adopt zero-trust models and implement stronger identity governance protocols.
This means investing in continuous training for employees, along with deploying tools like machine-identity detection and privileged-access management to secure every layer of access.
Outdated Software
Unpatched software remains one of the biggest entry points for attackers — 32% of cyberattacks in 2025 are linked to these known vulnerabilities.
Outdated PMS systems, third-party dependencies and widespread smart devices like door locks and in-room IoT amplify the risk.
Many hotels struggle to keep up with security patches due to vendor reliance or compatibility issues.
Addressing this requires adopting automated patch management tools, running regular vulnerability scans and maintaining an accurate inventory of all systems to identify and close gaps before they can be exploited.
Real-World Case Studies: Cybersecurity Lessons from the Field
Recent hospitality cyber incidents underline systemic weaknesses:
- Marriott International (2020): 5.2 million guest records were exposed due to stolen credentials. The breach revealed poor privilege access management.

- Booking.com (2022): Targeted with phishing schemes using fake reservation links to trick hotels into revealing portal credentials.
- Red Roof Inn (2023): Cyberattack exposed franchisee POS systems, forcing system-wide audits and protocol upgrades.
These case studies highlight the urgent need for hospitality cybersecurity strategies that prioritize endpoint protection, staff training and third-party risk mitigation.
Best Practices for Strengthening Hospitality Cybersecurity
The hospitality industry handles sensitive guest information daily, from credit card transactions to passport details. Strengthening hospitality cybersecurity is no longer optional — it’s a necessity for protecting both business operations and customer trust.
To stay ahead of threats, Hotel Managers and operators need clear, actionable strategies.
Some of the best practices include:
- Regular software updates: Keeping property management systems and booking platforms patched helps close vulnerabilities attackers often exploit.
- Employee training: Staff are often the first line of defense. Training them to recognize phishing attempts or suspicious links reduces the chance of human error leading to a breach.
- Multi-factor authentication (MFA): Adding an extra security layer to logins protects against compromised passwords.
- Network segmentation: Separating guest WiFi from internal systems helps prevent attackers from gaining access to sensitive data through public connections.
- Incident response planning: Having a documented, tested response plan ensures quick action if a breach occurs, minimizing financial and reputational damage.
By implementing these practices, hospitality businesses can significantly reduce their exposure to cyber risks and create a safer digital environment for both staff and guests.
Watch this video featuring Hotel-Spider CEO Marco Baurdoux, where he breaks down the most common social engineering threats facing hotels today — from phishing emails and spoofed messages to scam pop-ups — and shows staff how to build safer password practices.
Navigating Compliance: Regulations & Hotel Cybersecurity Obligations
The EU AI Act, which took effect on February 2, 2025, has signaled a shift toward stricter data privacy and transparency regulations.
Similar measures are emerging across U.S. states and other regions, creating a fragmented legal environment that hospitality businesses must navigate carefully.
The sector is especially vulnerable to copycat domain registrations, phishing scams and fake booking sites — areas often overlooked in compliance audits.
To stay compliant and competitive, hospitality organizations should audit their data flows, implement privacy-by-design principles and align with evolving AI regulations.
Monitoring domain misuse, deploying DMARC and HTTPS protocols and running regular phishing simulations should now be standard in any hotel’s cybersecurity playbook.
Final Thoughts On Cybersecurity in the Hospitality Industry
Cyber threats in hospitality are becoming more sophisticated, costly and frequent.
As guest-facing technologies evolve, so do the risks — ranging from AI-driven phishing to identity misuse and unpatched legacy systems.
In 2025, cybersecurity is a core business function, not just an IT issue. Hotels that prioritize real-time threat detection, zero-trust access controls and compliance with emerging regulations will be better positioned to protect their data, operations and reputation.
Building a resilient cybersecurity posture is now essential to delivering a secure and seamless guest experience.





Loading comments...